|
Other articles:
|
Information technology -- Open Systems Interconnection -- Structure of management information: Systems management application layer managed objects, 90.93 .
Application Layer Gateway - application level security and control . Protect servers without the need for a DMZ through application-friendly NAT traversal .
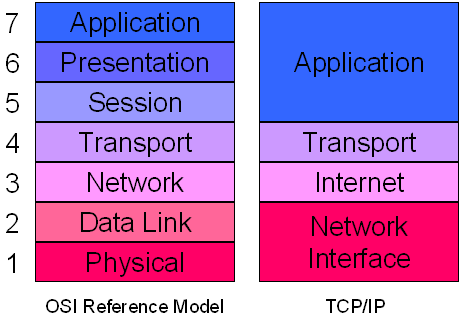
Oct 20, 2010 . The application layer is the seventh level of the seven-layer OSI model. It interfaces directly to and performs common application services .
Aug 3, 2000 . In the Open Systems Interconnection (OSI) communications model, the application layer provides services for an application program to ensure .
Oct 3, 2007 . The Application Layer, also known as Layer 7 of the OSI Reference Model, is the top layer of the model and provides the user interface to a .
![]() Mar 5, 2004 . In this chapter, we'll move further up the OSI Seven Layer Model and take an in- depth look at the workings of some of the Application layer .
ISA Server 2004 is an application-layer firewall, virtual private network, and Web cache server delivering Microsoft class security with simplified .
File Format: PDF/Adobe Acrobat - Quick View
The OSI model defines the application layer as being the user interface. The OSI application layer is responsible for displaying data and images to the user .
application layer The software in the OSI protocol stack (layer 7 of 7) that provides the starting point of the communications session.
Feb 20, 2011 . There are many Application layer protocols and new protocols are always . Examples of Application layer interfaces for TCP/IP applications .
Nov 11, 2010 . DDOSIM simulates several zombie hosts (having random IP addresses) which create full TCP connections to the target server.
1.1 Application layer: Provides a means for the user to access information on the network through an application. This layer is the main interface for the .
Feb 16, 2002 . Recently, we conducted a measurement study to gain insight about features of mirrored sites that will help in designing an application layer .
File Format: PDF/Adobe Acrobat - Quick View
Feb 2, 2004 . The latest Internet defense technology - deep packet inspection firewalls - is being touted as the best line of defense against worms that .
File Format: Microsoft Powerpoint - Quick View
Mar 5, 2004 . In this chapter, we'll move further up the OSI Seven Layer Model and take an in- depth look at the workings of some of the Application layer .
ISA Server 2004 is an application-layer firewall, virtual private network, and Web cache server delivering Microsoft class security with simplified .
File Format: PDF/Adobe Acrobat - Quick View
The OSI model defines the application layer as being the user interface. The OSI application layer is responsible for displaying data and images to the user .
application layer The software in the OSI protocol stack (layer 7 of 7) that provides the starting point of the communications session.
Feb 20, 2011 . There are many Application layer protocols and new protocols are always . Examples of Application layer interfaces for TCP/IP applications .
Nov 11, 2010 . DDOSIM simulates several zombie hosts (having random IP addresses) which create full TCP connections to the target server.
1.1 Application layer: Provides a means for the user to access information on the network through an application. This layer is the main interface for the .
Feb 16, 2002 . Recently, we conducted a measurement study to gain insight about features of mirrored sites that will help in designing an application layer .
File Format: PDF/Adobe Acrobat - Quick View
Feb 2, 2004 . The latest Internet defense technology - deep packet inspection firewalls - is being touted as the best line of defense against worms that .
File Format: Microsoft Powerpoint - Quick View


 Sep 24, 2010 . This layer supports application and end-user processes. . Tiered application architectures are part of this layer. .
Unfortunately, adoption of application layer security solutions by the industry has left much to be desired. Any number of valid reasons might be postulated .
Feb 2, 2011 . The Working Group will design and specify an Application-Layer Traffic . services (e.g. application-layer protocols for Internet .
File Format: PDF/Adobe Acrobat - Quick View
Mar 3, 2009 . Some of the hardest to mitigate distributed denial of service attacks are the ones targeting the application layer (in TCP/IP stack). .
Jan 27, 2008 . A lot of newcomers to TCP/IP wonder why an Application Layer is needed, since the Transport Layer handles a lot of interfacing between the .
File Format: Adobe PostScript - View as HTML
Sep 24, 2010 . This layer supports application and end-user processes. . Tiered application architectures are part of this layer. .
Unfortunately, adoption of application layer security solutions by the industry has left much to be desired. Any number of valid reasons might be postulated .
Feb 2, 2011 . The Working Group will design and specify an Application-Layer Traffic . services (e.g. application-layer protocols for Internet .
File Format: PDF/Adobe Acrobat - Quick View
Mar 3, 2009 . Some of the hardest to mitigate distributed denial of service attacks are the ones targeting the application layer (in TCP/IP stack). .
Jan 27, 2008 . A lot of newcomers to TCP/IP wonder why an Application Layer is needed, since the Transport Layer handles a lot of interfacing between the .
File Format: Adobe PostScript - View as HTML
 This chapter describes how to configure application layer protocol inspection. Inspection engines are required for services that embed IP addressing .
For example, the Application Layer Gateway Service listens for outgoing FTP traffic from an FTP client. It then extracts the port from which the FTP client .
Jan 7, 2009 . L7-filter is a classifier for Linux's Netfilter that identifies packets based on application layer data. It can classify packets as Kazaa, .
Application Layer Functions and Protocols (cisco ccna networking . - 4 min - Oct 3, 2009 - Uploaded by f9l1x
This chapter describes how to configure application layer protocol inspection. Inspection engines are required for services that embed IP addressing .
For example, the Application Layer Gateway Service listens for outgoing FTP traffic from an FTP client. It then extracts the port from which the FTP client .
Jan 7, 2009 . L7-filter is a classifier for Linux's Netfilter that identifies packets based on application layer data. It can classify packets as Kazaa, .
Application Layer Functions and Protocols (cisco ccna networking . - 4 min - Oct 3, 2009 - Uploaded by f9l1x

 Sep 9, 2010 . Fundamental principals to creating a comprehensive strategy for protecting your company against application layer attacks and data loss.
This article explains TCP/IP Application Layer Protocols, how they work and how they build upon the characteristics of TCP and UDP.
The application layer consists of what most users think of as programs. The application does the actual work at hand. Although each application is different .
May 31, 2006 . Application Layer [his name for Service Layer]: Defines the jobs the software is supposed to do and directs the expressive domain objects to .
Apr 15, 2004 . Back in the day, just before the launch of a dotcom I now regret being associated with, I asked our .
File Format: PDF/Adobe Acrobat - Quick View
Sep 23, 2008 . An overview of the application layer inspection filters that come with the ISA firewall right out of the box and the duties they perform.
Sep 9, 2010 . Fundamental principals to creating a comprehensive strategy for protecting your company against application layer attacks and data loss.
This article explains TCP/IP Application Layer Protocols, how they work and how they build upon the characteristics of TCP and UDP.
The application layer consists of what most users think of as programs. The application does the actual work at hand. Although each application is different .
May 31, 2006 . Application Layer [his name for Service Layer]: Defines the jobs the software is supposed to do and directs the expressive domain objects to .
Apr 15, 2004 . Back in the day, just before the launch of a dotcom I now regret being associated with, I asked our .
File Format: PDF/Adobe Acrobat - Quick View
Sep 23, 2008 . An overview of the application layer inspection filters that come with the ISA firewall right out of the box and the duties they perform.
 Jun 26, 2010 . If you are not using Internet Connection Sharing (ICS) service, the Application Layer Gateway Service and Internet Connection Sharing (ICS) .
Jun 26, 2010 . If you are not using Internet Connection Sharing (ICS) service, the Application Layer Gateway Service and Internet Connection Sharing (ICS) .

 In TCP/IP, the Application Layer contains all protocols and methods that fall into the realm of process-to-process communications across an Internet .
The Transmission Control Protocol/Internet Protocol (TCP/IP) application layer includes the functionalities specified in the Open System Interconnection .
In TCP/IP, the Application Layer contains all protocols and methods that fall into the realm of process-to-process communications across an Internet .
The Transmission Control Protocol/Internet Protocol (TCP/IP) application layer includes the functionalities specified in the Open System Interconnection .
 File Format: PDF/Adobe Acrobat - Quick View
File Format: PDF/Adobe Acrobat - Quick View
 File Format: PDF/Adobe Acrobat - Quick View
Jump to Layer 7: Application Layer: The Application Layer is the OSI layer closest to the end user, which means .
At the very top of the OSI Reference Model stack of layers, we find layer 7, the application layer. Continuing the trend that we saw in layers 5 and 6, .
File Format: PDF/Adobe Acrobat - Quick View
Jump to Layer 7: Application Layer: The Application Layer is the OSI layer closest to the end user, which means .
At the very top of the OSI Reference Model stack of layers, we find layer 7, the application layer. Continuing the trend that we saw in layers 5 and 6, .
.jpg)
 File Format: PDF/Adobe Acrobat
File Format: PDF/Adobe Acrobat
 File Format: PDF/Adobe Acrobat - Quick View
File Format: PDF/Adobe Acrobat - Quick View
 Application Layer, Perspective Branch. Picture of Connor on Deschutes River Or. where it comes into the Columbian River. "The more I study physics, the more .
Application Layer, Perspective Branch. Picture of Connor on Deschutes River Or. where it comes into the Columbian River. "The more I study physics, the more .
 The DSpace Web UI is the largest and most-used component in the application layer. Built on Java Servlet and JavaServer Page technology, it allows end-users .
Description of Application Layer from Tom Sheldon's Encyclopedia of Networking and Telecommunications.
The Application Layer is layer seven of the OSI model. The Application Layer resides above the Presentation Layer. The Application Layer of the OSI.
File Format: PDF/Adobe Acrobat - Quick View
The DSpace Web UI is the largest and most-used component in the application layer. Built on Java Servlet and JavaServer Page technology, it allows end-users .
Description of Application Layer from Tom Sheldon's Encyclopedia of Networking and Telecommunications.
The Application Layer is layer seven of the OSI model. The Application Layer resides above the Presentation Layer. The Application Layer of the OSI.
File Format: PDF/Adobe Acrobat - Quick View

 An application layer firewall controls access to Web applications and monitors for viruses and attacks that attempt to exploit security holes in .
Sitemap
An application layer firewall controls access to Web applications and monitors for viruses and attacks that attempt to exploit security holes in .
Sitemap
|











.jpg)

















.jpg)





