|
Other articles:
|
 4 posts - 2 authors - Last post: May 13I am brand new to SecureCRT, I am trying to find a way to create logs off a bastion host. IE, no main log file only log once I connect to .
Un bastión host es una aplicación que se localiza en un server con el fin de ofrecer seguridad a la red interna, por lo que ha sido especialmente .
It would be useful to have packages that reset the SUID files for examples situations such as Bastion Hosts (high), multi-user servers (medium), .
4 posts - 2 authors - Last post: May 13I am brand new to SecureCRT, I am trying to find a way to create logs off a bastion host. IE, no main log file only log once I connect to .
Un bastión host es una aplicación que se localiza en un server con el fin de ofrecer seguridad a la red interna, por lo que ha sido especialmente .
It would be useful to have packages that reset the SUID files for examples situations such as Bastion Hosts (high), multi-user servers (medium), .
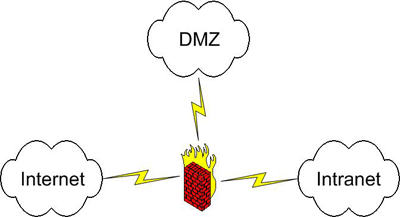 A bastion host is a computer that is fully exposed to attack. The system is on the public side of the demilitarized zone (DMZ), unprotected by a firewall or .
A bastion host is a computer that is fully exposed to attack. The system is on the public side of the demilitarized zone (DMZ), unprotected by a firewall or .
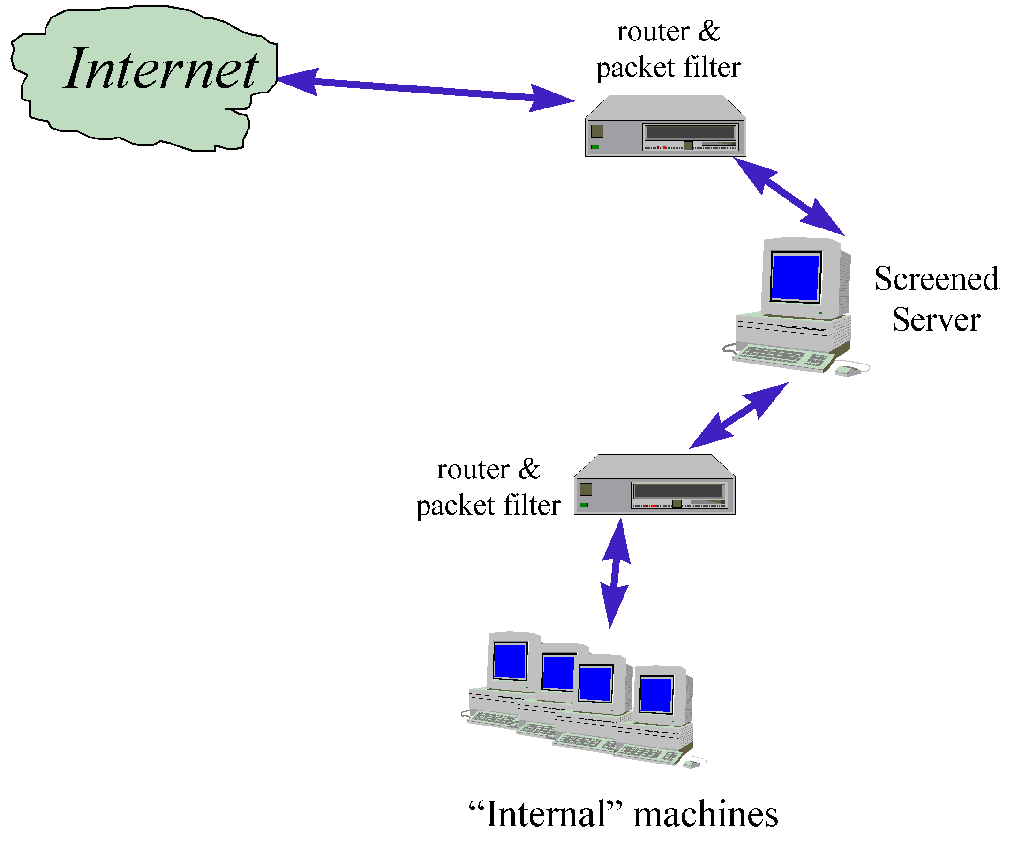 Apr 26, 2006 . This chapter focuses on how to harden bastion hosts that run Microsoft® Windows Server™ 2003 with Service Pack 1 (SP1) in your environment. .
Apr 26, 2006 . This chapter focuses on how to harden bastion hosts that run Microsoft® Windows Server™ 2003 with Service Pack 1 (SP1) in your environment. .
 Bastion Host Accounts. 29-August-08 04:19 PM Filed in: News. This is a reminder to returning students in the department, the Bastion Accounts that allow you .
The Bastion Host Security Service is one of a series of security measures implemented to ensure IET - Data Center and Client Service (DCCS) compliance with .
On the Internet, a bastion host is the only host computer that a company allows to be addressed directly from the public network and that is designed to .
A bastion host is your public presence on the Internet. Think of it as the lobby of a building. Outsiders may not be able to go up the stairs and may not be .
Bastion Host Accounts. 29-August-08 04:19 PM Filed in: News. This is a reminder to returning students in the department, the Bastion Accounts that allow you .
The Bastion Host Security Service is one of a series of security measures implemented to ensure IET - Data Center and Client Service (DCCS) compliance with .
On the Internet, a bastion host is the only host computer that a company allows to be addressed directly from the public network and that is designed to .
A bastion host is your public presence on the Internet. Think of it as the lobby of a building. Outsiders may not be able to go up the stairs and may not be .
 I attempted to make a bastion host that basically runs sendmail 8.10.1 > and sits in the DMZ of our network. It's responsibility is to accept > all incoming .
File Format: PDF/Adobe Acrobat - Quick View
I attempted to make a bastion host that basically runs sendmail 8.10.1 > and sits in the DMZ of our network. It's responsibility is to accept > all incoming .
File Format: PDF/Adobe Acrobat - Quick View
 The bastion host provides any services your site needs to access the Internet, or wants to offer to the Internet - services you don't feel secure providing .
The bastion host provides any services your site needs to access the Internet, or wants to offer to the Internet - services you don't feel secure providing .
 Like most users out there (I think) my systems are usually configured to allow ssh connections from a small handfull of trusted hosts or a bastion host.
Mar 14, 2011 . SSH to a server through a bastion host with a single command. With command-line SSH, it's easy, just do: ssh -t <intermediate> ssh .
Jun 26, 2009 . Explains how to set bastion host under Linux operating systems to improve network security.
This page describes the term bastion host and lists other pages on the Web where you can find additional information.
3 posts - 2 authors - Last post: Feb 13, 2005Running Data Protector 5.1 on Bastion Host on Windows 2003. . Which means we want to shut down services and create a bastion host. .
File Format: Microsoft Powerpoint - Quick View
A Bastion Host is a server that is configured such that the Operating System (OS ) is hardened for security. This type of configuration is used on Firewalls, .
A bastion host is a special purpose computer on a network specifically designed and configured to withstand attacks. The computer generally hosts a single .
Bastion Hosts in a Firewall. In this "screened subnet" firewall architecture, several bastion hosts reside in their own perimeter net, which is protected by .
Like most users out there (I think) my systems are usually configured to allow ssh connections from a small handfull of trusted hosts or a bastion host.
Mar 14, 2011 . SSH to a server through a bastion host with a single command. With command-line SSH, it's easy, just do: ssh -t <intermediate> ssh .
Jun 26, 2009 . Explains how to set bastion host under Linux operating systems to improve network security.
This page describes the term bastion host and lists other pages on the Web where you can find additional information.
3 posts - 2 authors - Last post: Feb 13, 2005Running Data Protector 5.1 on Bastion Host on Windows 2003. . Which means we want to shut down services and create a bastion host. .
File Format: Microsoft Powerpoint - Quick View
A Bastion Host is a server that is configured such that the Operating System (OS ) is hardened for security. This type of configuration is used on Firewalls, .
A bastion host is a special purpose computer on a network specifically designed and configured to withstand attacks. The computer generally hosts a single .
Bastion Hosts in a Firewall. In this "screened subnet" firewall architecture, several bastion hosts reside in their own perimeter net, which is protected by .
.gif) 2 posts - 1 author - Last post: Mar 31In my public subnet, I have a Bastion Host running openswan to enable VPN connections. This allows us to reach the private subnet. .
2 posts - 1 author - Last post: Mar 31In my public subnet, I have a Bastion Host running openswan to enable VPN connections. This allows us to reach the private subnet. .
 File Format: PDF/Adobe Acrobat - Quick View
File Format: PDF/Adobe Acrobat - Quick View
.gif) Oct 16, 2002 . A bastion host is a computer system that is exposed to attack, and may be a critical component in a network security system. .
May 17, 2004 . This paper presents a methodology for building a bastion host using HP-UX 11, and walks through the steps used to build a sample, .
Oct 16, 2002 . A bastion host is a computer system that is exposed to attack, and may be a critical component in a network security system. .
May 17, 2004 . This paper presents a methodology for building a bastion host using HP-UX 11, and walks through the steps used to build a sample, .




 A bastion host is your public presence on the Internet. Think of it as the lobby of a building. Outsiders may not be able to go up the stairs and may not be .
Description of Bastion Host from Tom Sheldon's Encyclopedia of Networking and Telecommunications.
img023, First · Previous · Next · Last · Index · Home. Slide 23 of 26.
A Bastion host is a network system that may be exposed to attack from other internal or external network systems. Because of this, every effort must be made .
Bastion hosts should be located on a network that does not carry confidential traffic, preferably a special network of their own. .
Bastion host - Description: A bastion host is a special purpose computer on a network specifically designed and configured to withstand attacks.
Collection of news articles, blog posts, white papers, case studies, videos and comments relating to bastion host.
A bastion host is your public presence on the Internet. Think of it as the lobby of a building. Outsiders may not be able to go up the stairs and may not be .
Description of Bastion Host from Tom Sheldon's Encyclopedia of Networking and Telecommunications.
img023, First · Previous · Next · Last · Index · Home. Slide 23 of 26.
A Bastion host is a network system that may be exposed to attack from other internal or external network systems. Because of this, every effort must be made .
Bastion hosts should be located on a network that does not carry confidential traffic, preferably a special network of their own. .
Bastion host - Description: A bastion host is a special purpose computer on a network specifically designed and configured to withstand attacks.
Collection of news articles, blog posts, white papers, case studies, videos and comments relating to bastion host.
 Bastion. This service is used to access the DESY network via SSH. Simply connect with your local SSH client to bastion.desy.de and login with your AFS .
File Format: Microsoft Powerpoint - Quick View
Bastion. This service is used to access the DESY network via SSH. Simply connect with your local SSH client to bastion.desy.de and login with your AFS .
File Format: Microsoft Powerpoint - Quick View
 Bastion hosts are used for services such as Web site hosting, mail, DNS lookups and FTP transfer and are located on the public side of a perimeter net (DMZ) .
Bastion hosts are used for services such as Web site hosting, mail, DNS lookups and FTP transfer and are located on the public side of a perimeter net (DMZ) .
 A bastion host is a special purpose computer on a network specifically designed and configured to withstand attacks. The computer generally hosts a single .
A bastion host is a special purpose computer on a network specifically designed and configured to withstand attacks. The computer generally hosts a single .
 topologies, including diagrams of a bastion host, screened subnet and dual- firewall architectures. Placing systems in a firewall topology: .
81%. LOADING BASTIONHOST.
Return to Bastionhost. DATAVILLE. Click to enquire about Dataville services. Connectivity. Custom Data Centers. Managed Hosting. Hot Parking .
4 posts - 2 authors - Last post: Feb 7Is there any way to set up a GUI editor to ssh through a bastion host. I currently use Coda/Transmit but I recently got a project that .
File Format: PDF/Adobe Acrobat - Quick View
Copy & paste this link to your blog or website to reference this page. Added to Favorites. Related Searches. Bastion host diagram .
topologies, including diagrams of a bastion host, screened subnet and dual- firewall architectures. Placing systems in a firewall topology: .
81%. LOADING BASTIONHOST.
Return to Bastionhost. DATAVILLE. Click to enquire about Dataville services. Connectivity. Custom Data Centers. Managed Hosting. Hot Parking .
4 posts - 2 authors - Last post: Feb 7Is there any way to set up a GUI editor to ssh through a bastion host. I currently use Coda/Transmit but I recently got a project that .
File Format: PDF/Adobe Acrobat - Quick View
Copy & paste this link to your blog or website to reference this page. Added to Favorites. Related Searches. Bastion host diagram .
 The bastion host does not provide intranet services itself. When it receives a request from the Internet for an intranet service, the host passes the .
The bastion host should be located on a network that does not carry confidential traffic, preferably a special network of its own. .
by C Cant - Cited by 4 - Related articles
Jun 9, 2010 . A bastion host or screening host, as it is sometimes called, uses both a packet filtering mechanism provided by the router plus a secured .
The bastion host does not provide intranet services itself. When it receives a request from the Internet for an intranet service, the host passes the .
The bastion host should be located on a network that does not carry confidential traffic, preferably a special network of its own. .
by C Cant - Cited by 4 - Related articles
Jun 9, 2010 . A bastion host or screening host, as it is sometimes called, uses both a packet filtering mechanism provided by the router plus a secured .
 A bastion host is typically a firewall implemented on top of an operating system that has been specially configured and hardened to be resistant to attack. .
Nov 16, 2010 . I need to remotely access a machine on a network accessible only through a bastion host. Currently I'm just sshing to the bastion, .
Most of this chapter discusses bastion hosts that are screened hosts or service- providing hosts on a screened network. There are several kinds of bastion .
5 posts - 3 authors - Last post: Apr 25, 2006[Archive] Bastion Host - Some Confusion? Firewall & Honeypot Discussions.
Sitemap
A bastion host is typically a firewall implemented on top of an operating system that has been specially configured and hardened to be resistant to attack. .
Nov 16, 2010 . I need to remotely access a machine on a network accessible only through a bastion host. Currently I'm just sshing to the bastion, .
Most of this chapter discusses bastion hosts that are screened hosts or service- providing hosts on a screened network. There are several kinds of bastion .
5 posts - 3 authors - Last post: Apr 25, 2006[Archive] Bastion Host - Some Confusion? Firewall & Honeypot Discussions.
Sitemap
|





.gif)

.gif)















.gif)

.gif)









